Email Security Best Practices: Your Ultimate Guide to Safe Communication

Table of contents
Remember the Gmail phishing attack of 2017? Hackers sent emails to Gmail users, asking them to open a malicious link. The result? Over 1 million Gmail users were infected with malware.
Email security is a tricky subject. If you have important business emails, bank transaction details, and other sensitive information all in your inbox, how do you keep them protected?
Let’s talk about some practical ways to strengthen email security.
Table of Contents
- 1. Use Strong, Unique Passwords
- 2. Enable Two-Factor Authentication (2FA)
- 3. Be Wary of Unsolicited Attachments and Links
- 4. Check the Email Address, Not Just the Display Name
- 5. Keep Software Updated
- 6. Use Encryption for Sensitive Information
- 7. Beware of Phishing Scams
- 8. Don’t Use Public Wi-Fi for Checking Emails
- 9. Regularly Review Account Activity
- Conclusion
1. Use Strong, Unique Passwords
Your password is the first line of defense against unwanted intruders. Just as you wouldn’t use a flimsy lock on your front door, you shouldn’t use weak passwords for your accounts.
You might be tempted to use passwords that are too simple and contain your basic information so that you can remember them whenever you need to log in. An example would be your birthdate or a combination of your birthdate and name, like Sara1409.
But the problem with this is that it is easy for intruders to guess them if they have some basic information about you. Instead, try to add special characters that resemble the letters to make it more complex.
So, Sara1409 can become something like $@r@_1409.
Password managers, such as Bitwarden and Dashlane, are lifesavers here. They generate and store complex passwords for every account, ensuring you don’t reuse them.
2. Enable Two-Factor Authentication (2FA)
This is the digital equivalent of a double-locked door. This makes sure that even if an intruder somehow gains access to your password, they need another level of authentication to gain access to your email.
Gmail, for instance, asks users to enable 2FA to ensure email security — you can skip it, but it’s not the best practice.
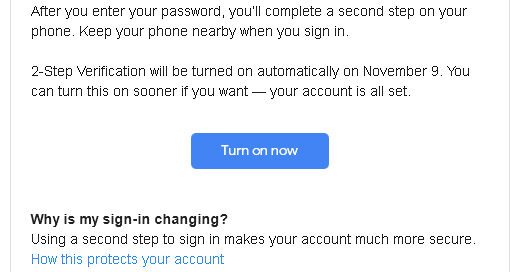
There are multiple 2FA methods, such as SMS codes, authentication apps, or even physical keys like YubiKey.
Here’s how 2FA works: You enter your password to log into an account. Immediately, your phone buzzes with a unique, time-sensitive code. Only upon entering this code do you gain access.
3. Be Wary of Unsolicited Attachments and Links
Not all that glitters is gold — at least at first glance. Sometimes, you might receive tempting emails with attachments or links that may seem legitimate when you first look at them. But this can lead to a security breach.
Ensure your email client can scan attachments for malware. When in doubt, verify the legitimacy of emails through other communication means.
Say, you receive an email with the subject “Invoice Attached” from a vendor you don’t recognize. Instead of immediately opening the attachment, you should contact the vendor directly to verify its authenticity.
4. Check the Email Address, Not Just the Display Name
Names can be deceptive in the email world. Scammers can easily spoof display names to impersonate someone you trust. You may think you got an email from your boss or a dear friend, but if you simply take a closer look, you can ensure your email stays secure.
Delve into the email header or hover over the sender’s name. This shows the true email address and can help you identify malicious intent.
Say you see an email from “Your Boss – John.” But on closer inspection, the email is from “[email protected]” instead of “[email protected].”
It’s important to spot any irregularities in the email, even if it seems very close to the actual one.
5. Keep Software Updated
If your email client were a fortress, think of software patch management as reinforcements against new siege tactics.
Hackers exploit outdated software vulnerabilities. By keeping your email client, operating system, and other related software up-to-date, you close these vulnerable gaps.
Let’s consider a scenario where you ignored an update notification for your email client. A hacker aware of a security flaw in the older version sends a malicious email, gaining access to your device.
This scenario is more probable than you’d think. Updating the digital platforms you use regularly can help you patch such vulnerabilities.
6. Use Encryption for Sensitive Information
Think of encryption as a secret language only you and your recipient understand.
Picture sending a diary via mail. Without encryption, it’s as if you’re sending clear pages for anyone to read — which can easily be used for purposes you didn’t intend it to.
With encryption, anything sent is scrambled into gibberish, decipherable only with the right key. There are two main types of email encryption you can use:
- Transport Layer Security (TLS) encryption is already used by most major email providers, such as Gmail, Outlook, and Yahoo Mail. This basically means that your email is protected in transit.
- End-to-end encryption ensures that your emails are secure not just during transmission but also while stored. This prevents intermediaries from snooping and stealing your data. You can get end-to-end encryptions for free with email services like Proton Mail or TutaNota.
7. Beware of Phishing Scams
Phishing is when scammers bait you into giving personal information using seemingly legitimate emails. Don’t bite!
These malicious emails often urge immediate action, exploiting fear or urgency. They may mimic brands or people you trust. Always verify before you act.
Imagine receiving an email from “Netflix” stating there’s an issue with your payment. The login page looks legit, but the URL is slightly off. Logging in could hand your credentials to criminals.
A close cousin of phishing scams that you might have heard of is the famous Nigerian Prince scam or a 419 scam. It is now a running joke and has been a source of memes for decades — but it has actually had a lot of victims.

This is where you receive an email from a “Nigerian Prince” who needs your bank account information and personal details to transfer a huge amount of money to your bank account.
What happens next is you’re left with no money in your bank account, and the prince never comes to the rescue. The lesson here is some things that seem too good to be true might actually be a scam — so beware.
8. Don’t Use Public Wi-Fi for Checking Emails
Many times, you may have stepped out of the house without a data plan. A cafe sign reads “Free WiFi,” — and a cup of coffee sounds good while you go through your social media feed or check your emails.
But public Wi-Fi, like in cafes or airports, is often unsecured. Accessing emails here is like discussing secrets in a crowded room.
If you must connect, use a Virtual Private Network (VPN). This creates a secure “tunnel” for your data, making interception much harder.
What is Virtual Private Network (VPN)?
A VPN is like a tunnel that encrypts your internet traffic and hides your IP address. This makes it more difficult for people to track what you are doing online. For example, if you are in the United States and connect to a VPN server in Germany, it will look like you are browsing the internet from Germany.
Say you do connect to a public Wi-Fi network at a coffee shop. Anyone who is also connected to that network could potentially see what websites you are visiting and what data you are sending and receiving. If you connect to a VPN, your traffic will be encrypted and your IP address will be hidden, making it much more difficult for anyone to snoop on your activities.
9. Regularly Review Account Activity
Monitoring your account isn’t just about tracking emails but keeping an eye out for suspicious activities.
Automated setups, rules, or filters you didn’t establish can be red flags. Unauthorized access might result in emails being auto-forwarded or deleted without your knowledge.
Say you notice that emails from a specific colleague consistently land in the trash. This could indicate that someone tampered with your settings. This is a call to change your passwords, sign out of all the devices, and take measures to secure your email.
Conclusion
Safe emailing isn’t about being paranoid; it’s about being prepared and informed. The digital realm is an ever-evolving space, and the threats change as swiftly as the technologies. By adhering to these best practices and staying up-to-date, you not only safeguard your personal and professional data but contribute to a more secure and trustworthy online environment for everyone.
Remember, each time you double-check that sender or think twice before clicking on a suspicious link, you’re taking one more step towards a safer digital world. So, here’s to making our inboxes a fortress, one email at a time.